Quantifying Risk is on the one hand a tough proposition, but on the other it is very essential to get a firm grip over Risk Management, and obtain stakeholder buy-in. Cyber Risk has emerged as a critical business risk that all entities need to deal with - from enterprises to individuals, from education and research establishments to Governments.
There are several frameworks that suggest a variety of approaches to Risk Management. The approach enumerated below is a hybrid approach borrowing from several frameworks with a focus on quantification of risk measurement and risk management. I have had the opportunity to witness it in practice in Operational Risk Management domains including Cyber Risk. The approach encompasses quantification of risk at all steps in an end-to-end Risk Management Lifecycle - from inherent risk to residual risk to risk acceptance, transfer and mitigation.
A: Risk Heat Map:
The following steps enumerate the process of assessing risks with a view to create a risk heat-map.
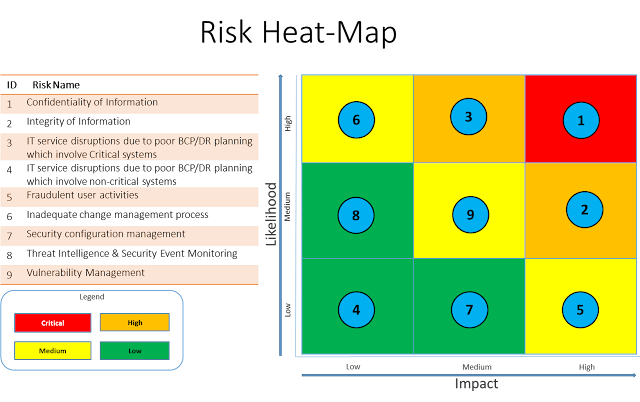
1. Create a Risk Inventory: Build an inventory of risk outcomes applicable to the specific entity being assessed by considering all types of assets, their inherent vulnerabilities, and the relevant threat vectors and actors which can exploit those vulnerabilities. Given here is a list of Cyber Risks:
The following steps enumerate the process of assessing risks with a view to create a risk heat-map.
1. Create a Risk Inventory: Build an inventory of risk outcomes applicable to the specific entity being assessed by considering all types of assets, their inherent vulnerabilities, and the relevant threat vectors and actors which can exploit those vulnerabilities. Given here is a list of Cyber Risks:
2. Compute Inherent Risk: Evaluate impact and likelihood of each risk; compute inherent risk severity for all risks (4 to 1 - Critical, High, Med, Low) by compounding their Impact and Likelihood.
B: Risk-Control Matrix (RCM):
1. Map all risks to the corresponding and relevant controls
C: Inherent Risk:
1. Define levels of effectiveness for all controls (1 to 4 - completely effective, mostly effective, not effective, not present)
2. For all instances where risks map to controls in the RCM, multiply the risk severity level (values 1 to 4 - critical, high, medium, low), and the level of control effectiveness required to mitigate the risk (default value of 4)
4. Add up all the numbers and that score represents inherent risk
D: Control Effectiveness Evaluations:
1. Evaluate all controls and score them as per their current level of control effectiveness (generic definitions of all four levels to be drafted,and current state compared to generic definition - default is 1 unless demonstrated otherwise )
E: Residual Risk:
1. For all instances where risks map to controls, multiply the risk severity level number and the current level of control effectiveness
2. . Add up all the numbers and this score represents current residual risk
3. Compute the % of current residual risk against inherent risk
F. Target State:
1. For all instances where risks map to controls, multiply the risk severity level number and the matching level of control effectiveness; if risk is critical (R=4), the control effectiveness must be completely effective (C=1), and similarly if risk is high(R=3), the control effectiveness must be mostly effective (C=2)
2. Add up all the numbers and this score represents target residual risk
3. Compute the % of target residual risk against inherent risk
G. Risk Mitigation Road-map:
1. Compute the differential of average control rating per security domain/category
2. Organize the security domains/categories in order from highest to lowest differential
3. Set thresholds of differentials to high, medium, and low categories
4. Map security domains/categories to corresponding risk mitigation projects in order of priority from high to low
5. Assign the current to target residual risk % differential proportionately between high(50% of differential), medium (30%), and low (20%) category projects, and further divide it equally among the projects within the categories
6. As the projects complete, the target residual risk will be achieved

No comments:
Post a Comment